Google Workspace: Create New User
Overview
The Google Workspace: Create New User Automation is an Extension Automation that can be applied to the current Staff Onboarding Automation (available for Cloud Only, Cloud Hybrid and Semi-Hybrid clients).
This document details how to complete the Google Workspace setup, complete the required Azure Key Vault Configuration, and configure the automation on a per client basis + attach to the current Staff Onboarding Automation.
Table of Contents
- Step 1: Google Workspace Configuration
- Step 2: Azure Key Vault Secret Creation
- Step 3: Extension Automation Configuration
Step 1: Google Workspace Configuration
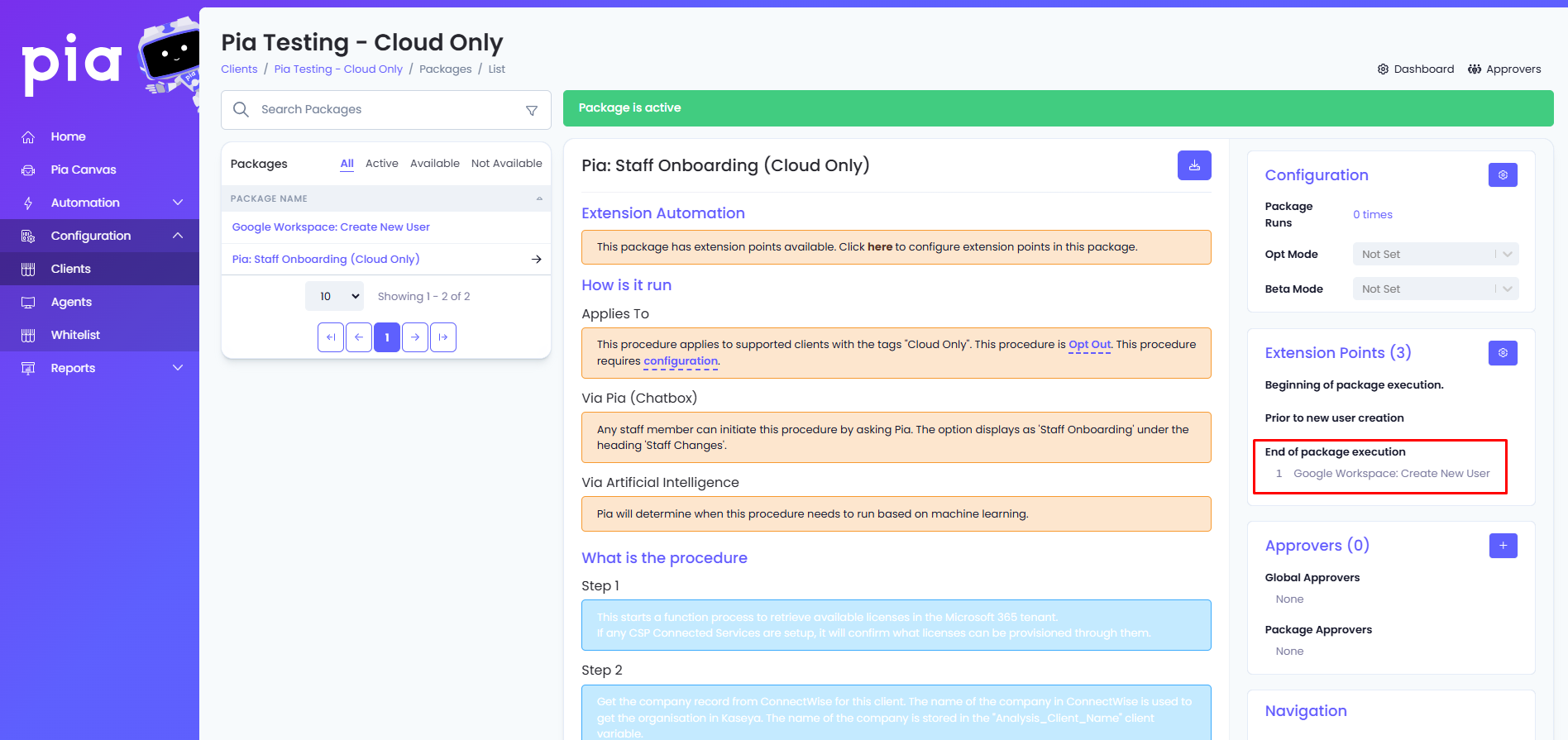
1a: Create a New Google Workspace Project
Navigate to New Google Workspace Project and create a New Project.
- Enter a Project name (*),
- assign the project to the Organization (*) (the domain of the client's environment),
- Location (*) auto populates to match Organization.
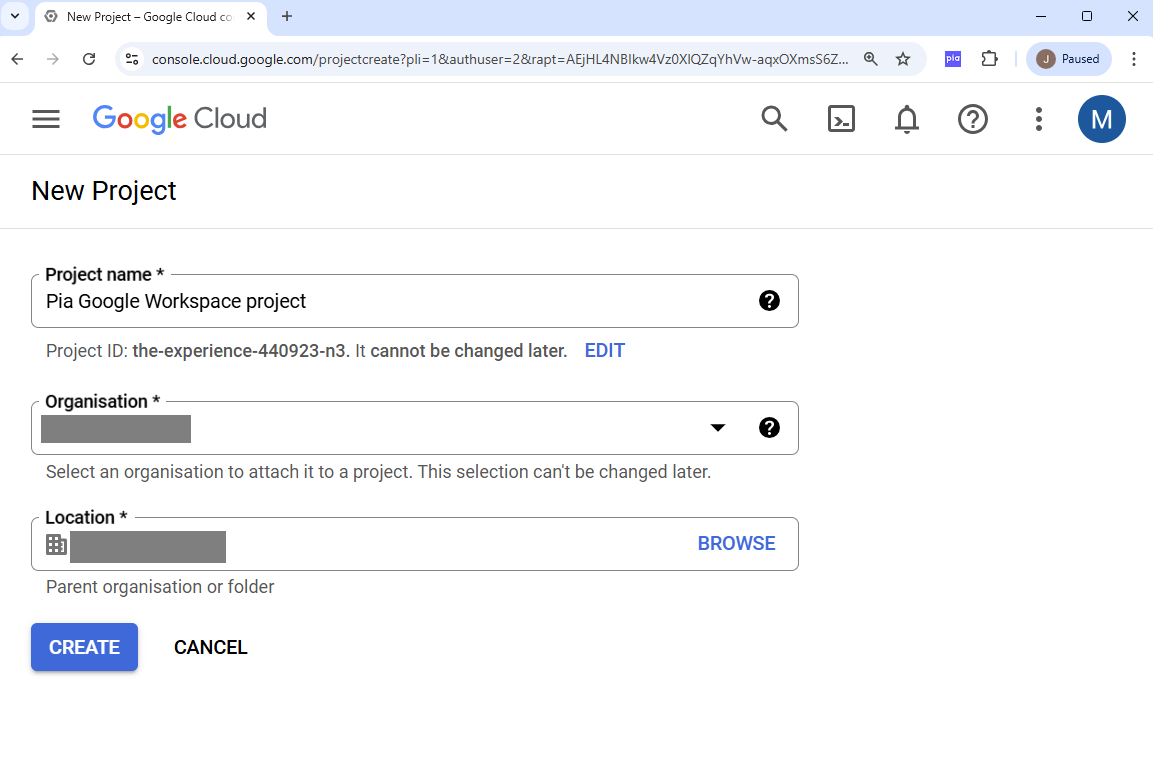
1b: Create a new Service account dedicated for Pia usage
Navigate to the Google APIs and Services Credentials page, your new Project should show in the top left hand dropdown.
Select + CREATE CREDENTIALS > Service account.
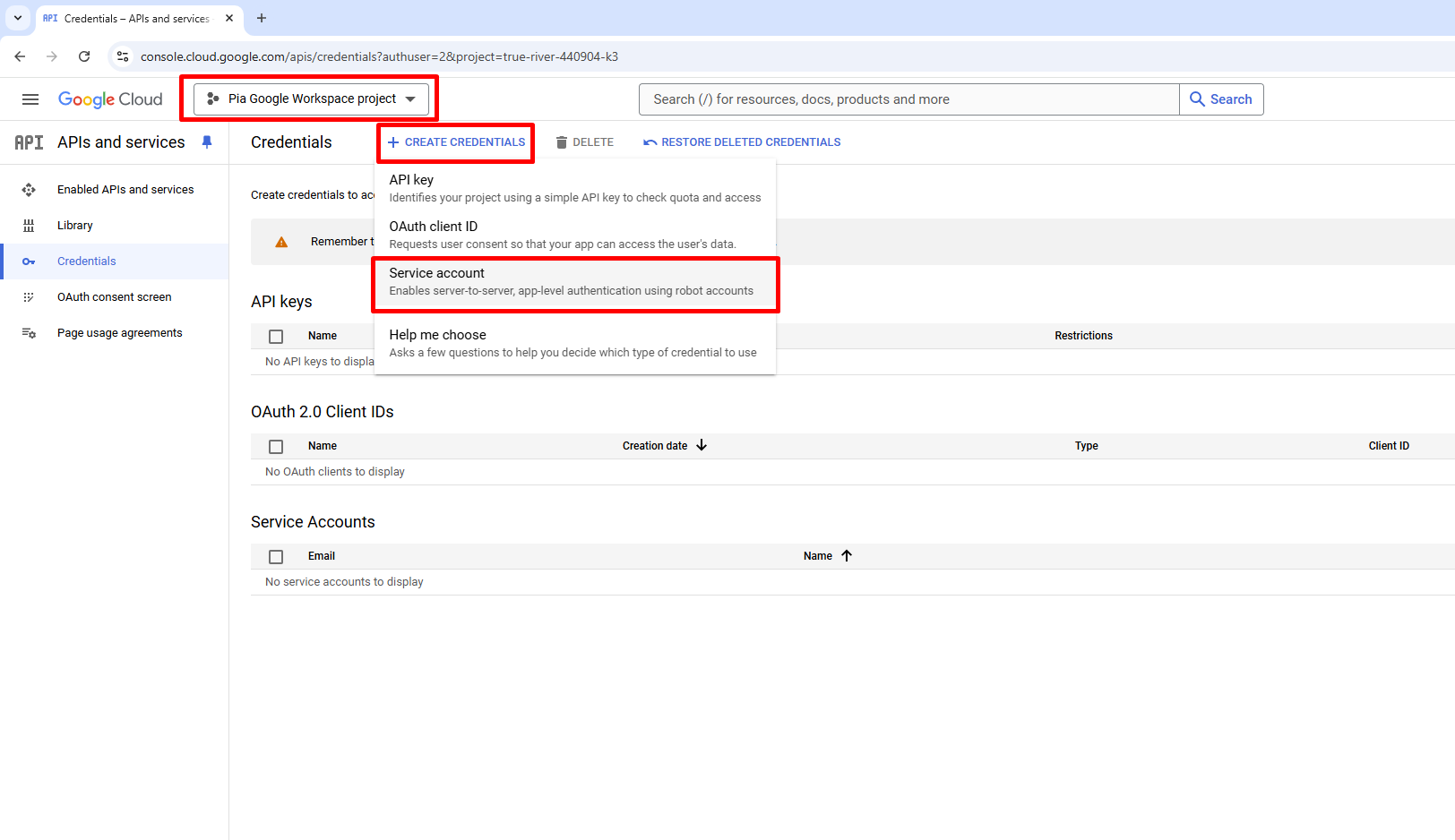
Then assign the new Service account name with a friendly name. The Service account ID (*) will auto populate. There is no need to assign the new Service account with any roles just yet, so click CREATE AND CONTINUE, we will simply finish the creation of the account. Then select "Done".
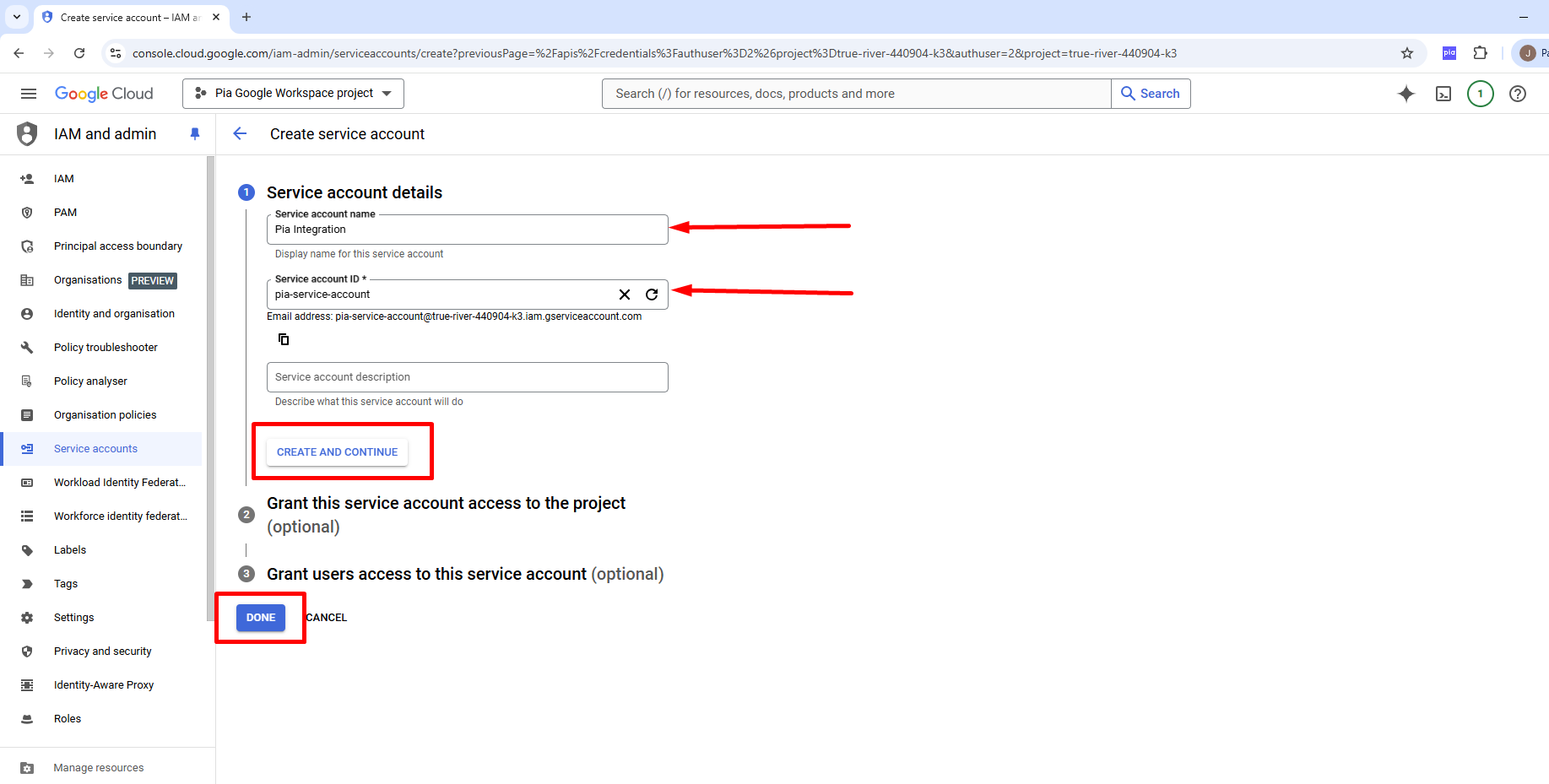
1c: Create a new key for your Service account
The newly created Service account will now show under Service accounts. Next, generate a key for the account by selecting the pencil (edit) icon on the right side of your account.
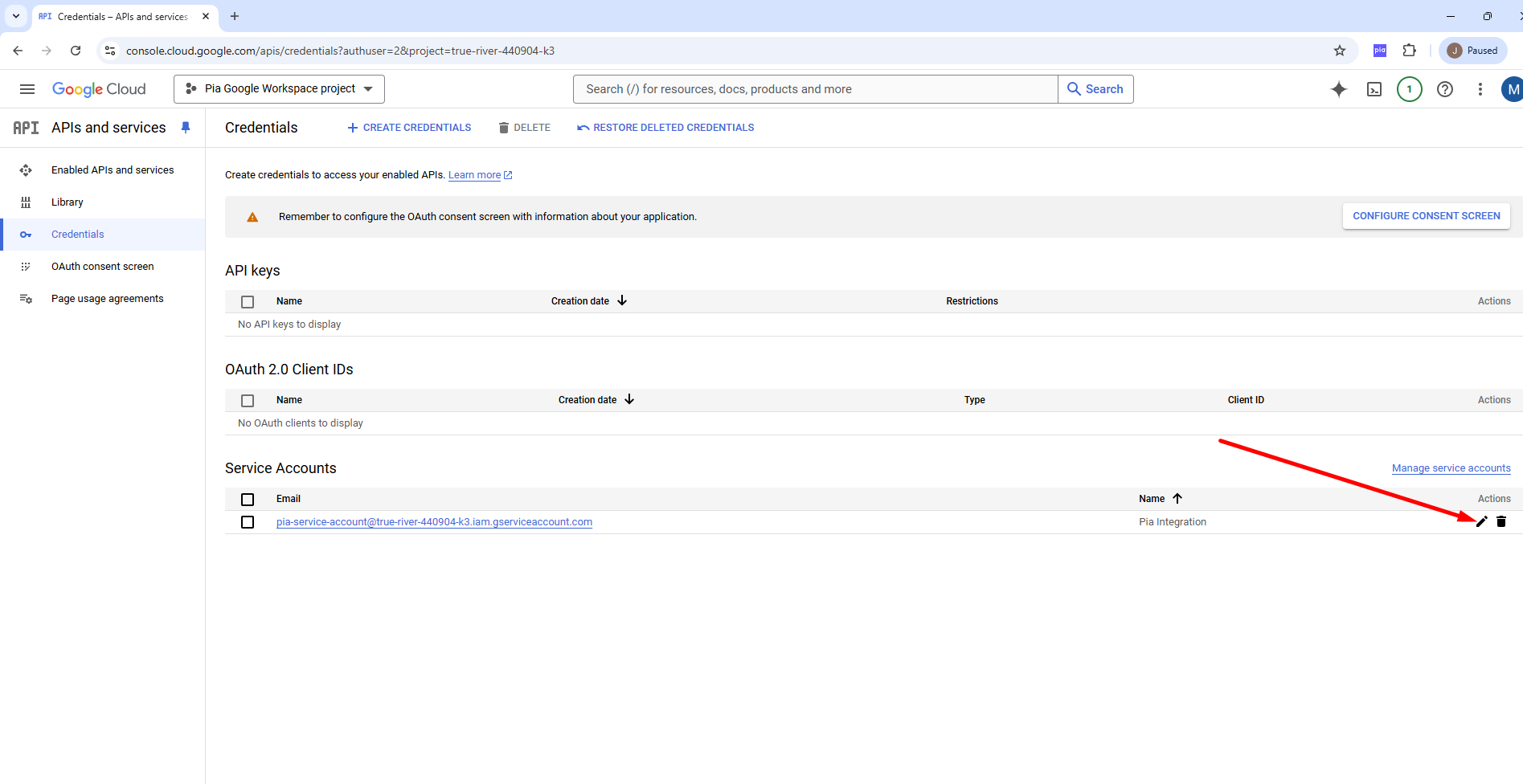
Navigate to the KEYS tab and select ADD KEY > Create new key.
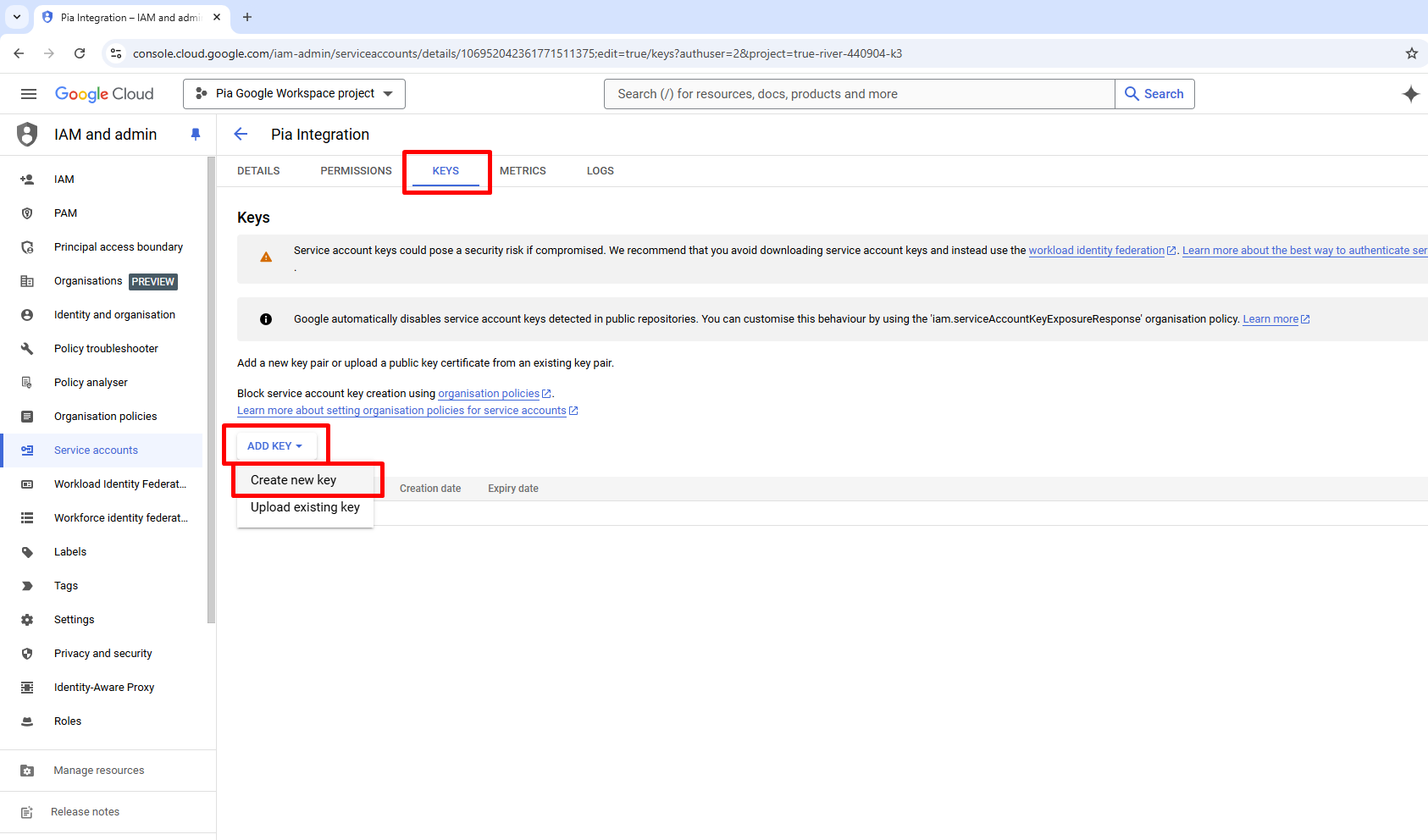
Once prompted for the Key type, you will need to select “JSON” and **CREATE. A file will be downloaded within your browser with the details of the newly created key (do not lose this file).
1d: Assign Roles to the newly created Service account
Now that you have created your Service account and generated your Key, navigate to https://admin.google.com/u/2/ac/roles and assign the “User Management” and “Groups Admin” roles to our Service account.
Select Assign admin beside the role (as seen below).
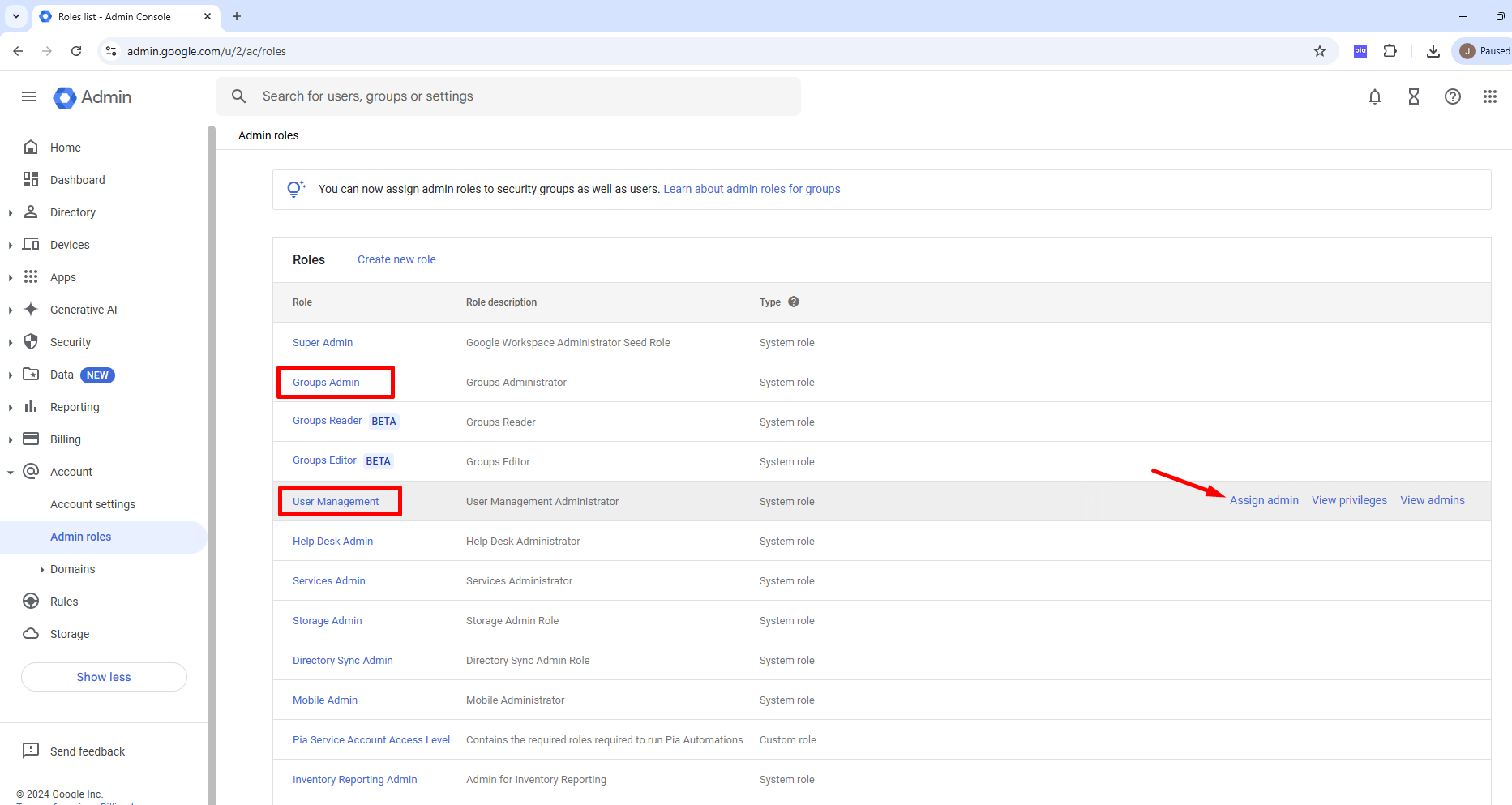
Under Admins, select Assign service accounts.
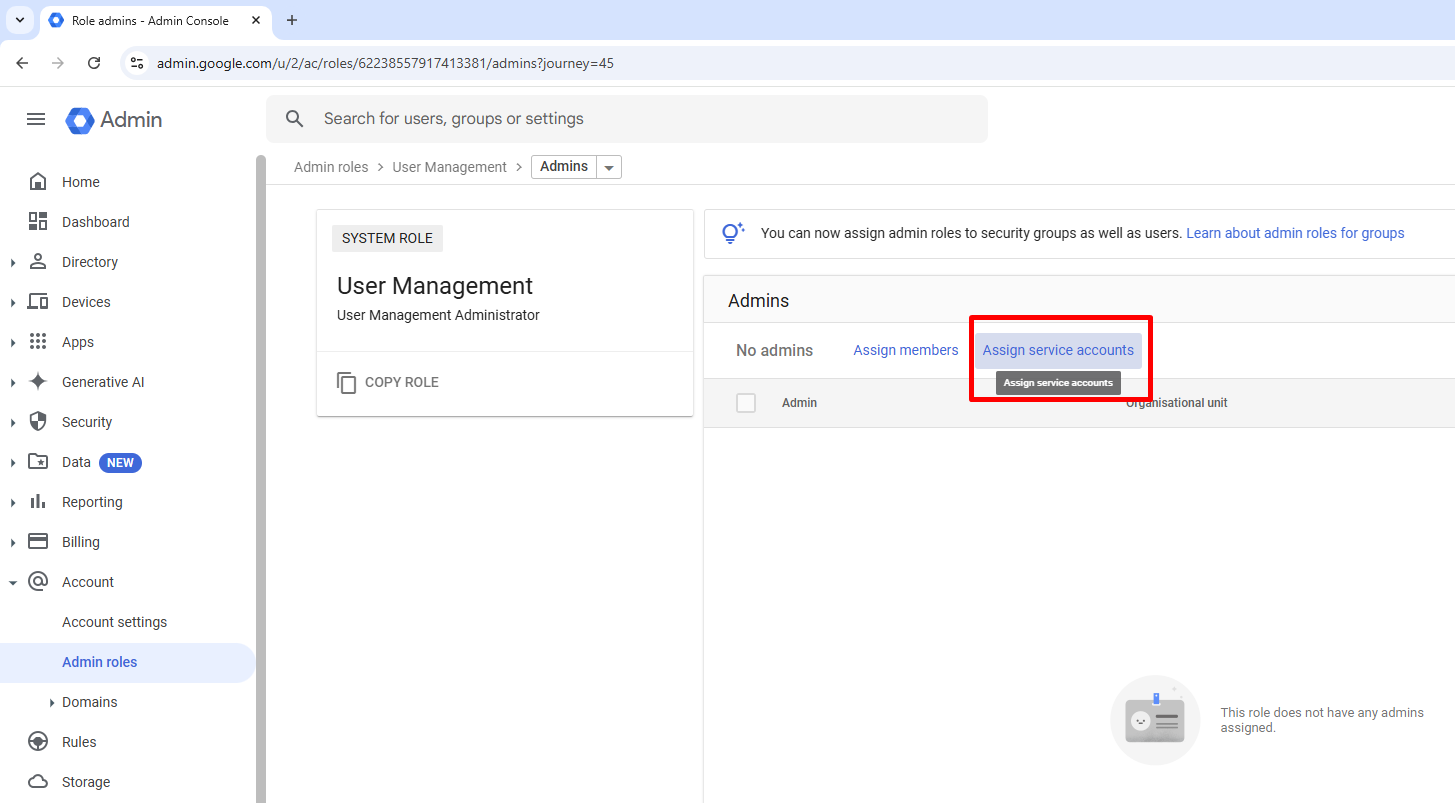
Enter the email (id) of your new service account (in our example case “pia-service-account@true-river-440904-k3.iam.gserviceaccount.com”) then select Add and Assign Role.
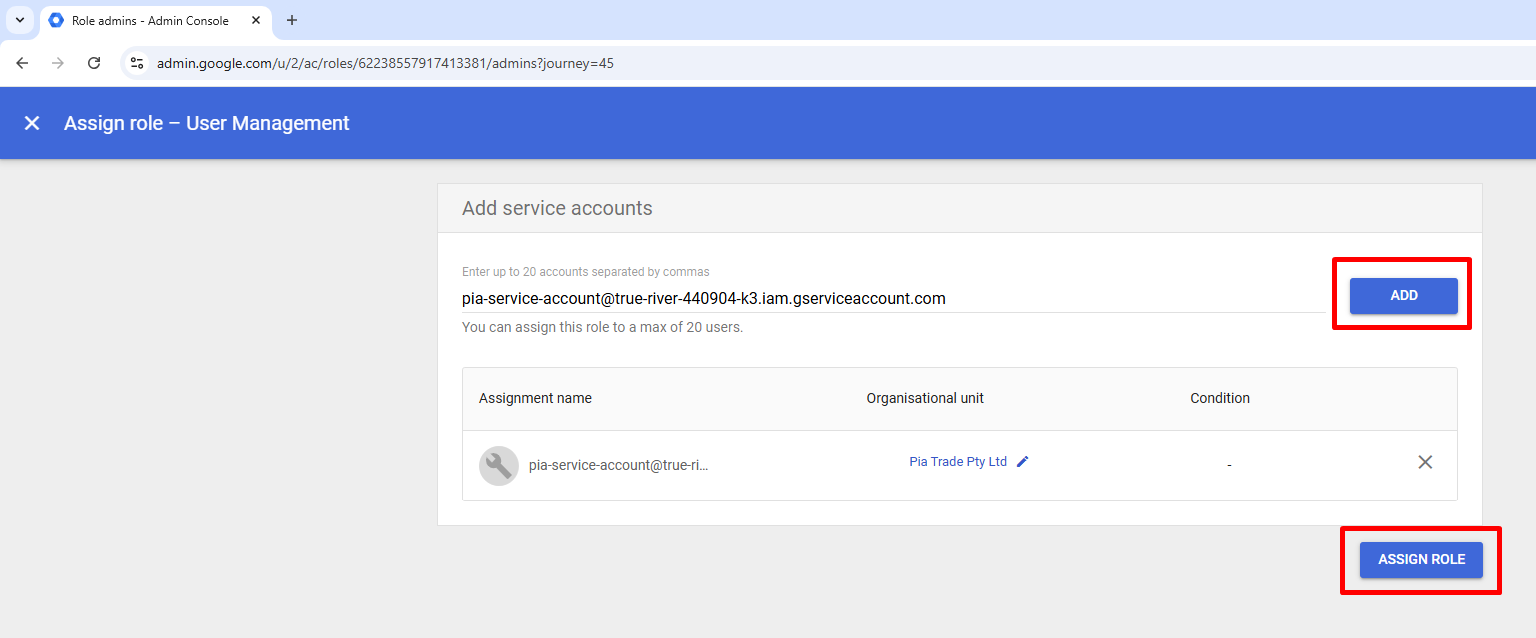
Repeat 1d for additional roles.
You have now assigned sufficient privileges to manage users within Google Workspace via a Service account!
Proceed to the next step.
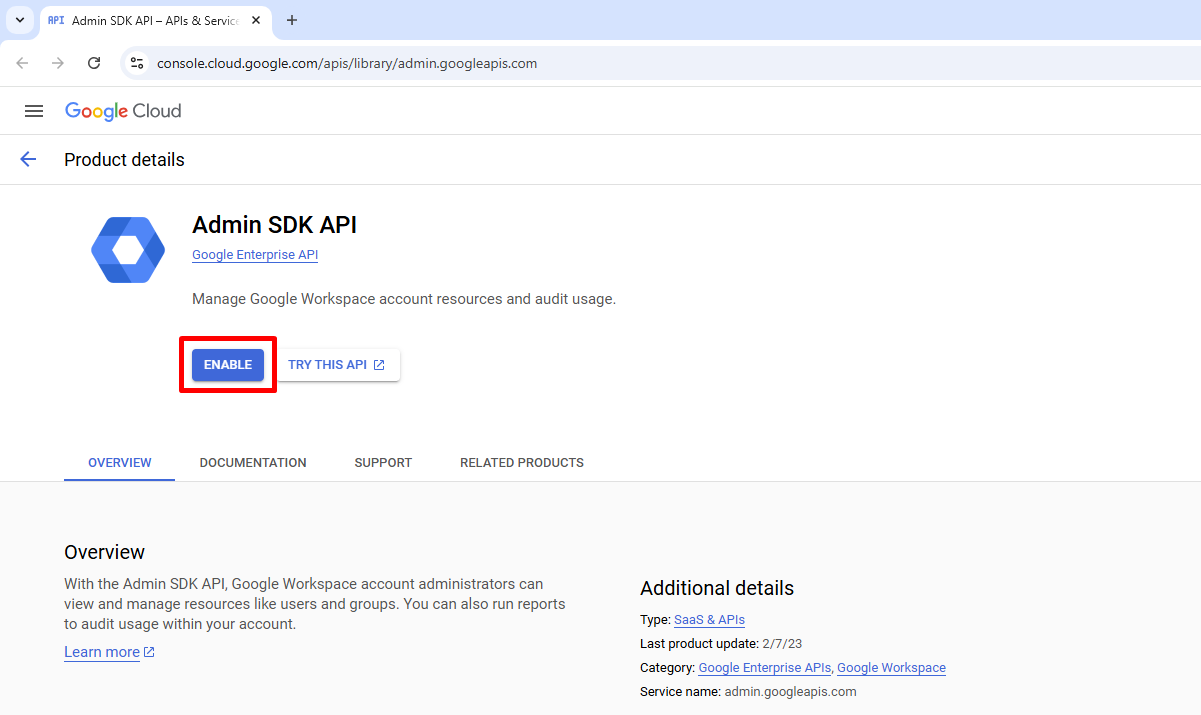
1e: Enable Admin SDK API
Navigate to https://console.cloud.google.com/apis/library/admin.googleapis.com where you can now ENABLE the Admin SDK API.
Step 2: Azure Key Vault Secret Creation
2a: Create Vault storage for Service account Private Key
Head over to Azure Key Vaults, if already created, select the desired Key Vault where you want to store the Google Workspace Private Key (if you are yet to create any vaults for your client, please visit Microsoft's Quickstart: Create a key vault using the Azure portal to assist in the creation).
Select the client key vault, then in menu select Objects > Secrets, then click + Generate/Import.
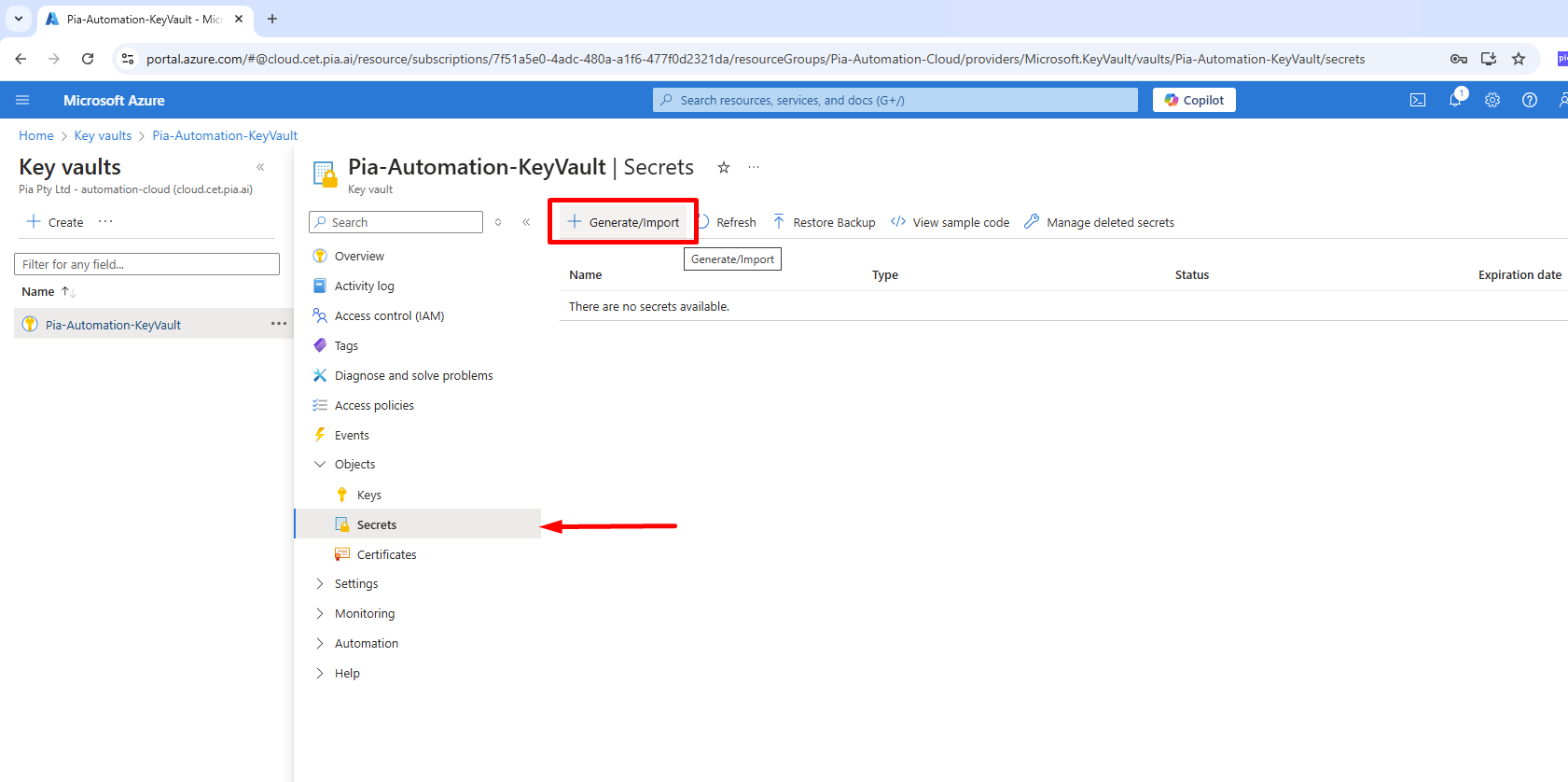
The Create a secret screen opens.
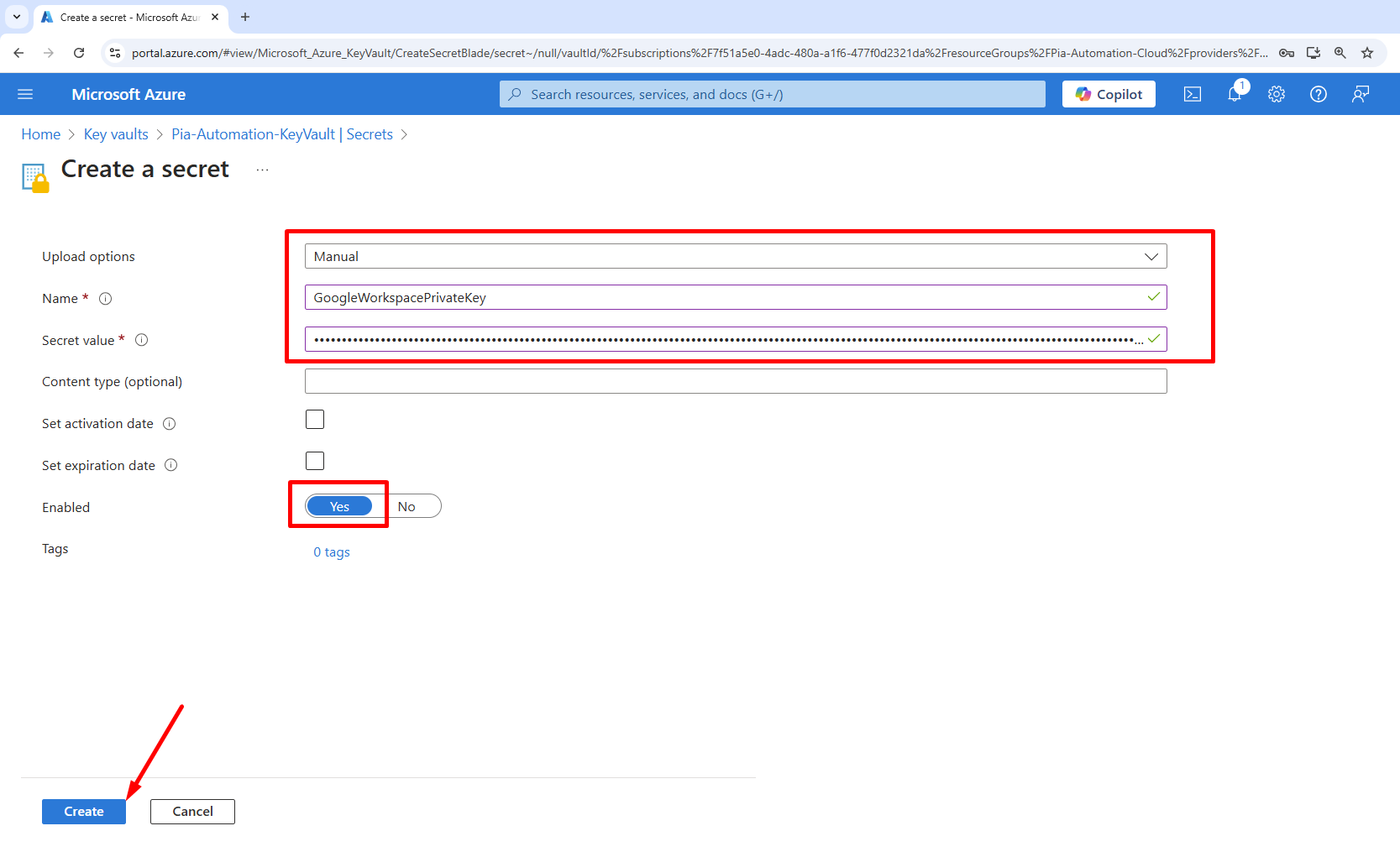
- Name (*): “GoogleWorkspacePrivateKey”.
- Secret value (*): you will need to access your serviceAccount .json file created from the "Create a new key for your Service account" tab.
Copy and paste the “private_key” value starting with “-----BEGIN PRIVATE KEY-----” and ending with “-----END PRIVATE KEY-----\n”.
Do not format this key, it is handled within the automation.
2b: Allow the Pia App Registration to read keys from the Vault
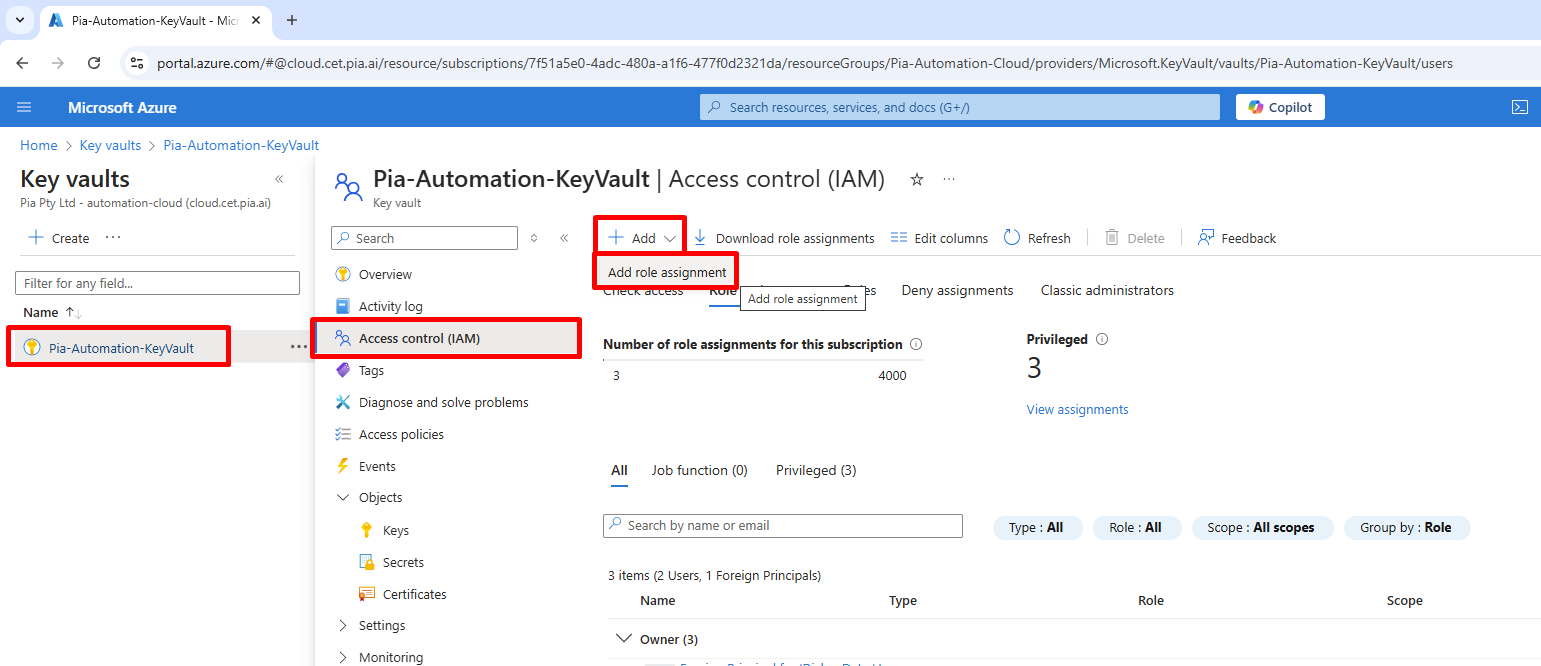
In order to allow our Pia application consent to read keys from the vault, you will need to head over to the client key vault within Azure Key Vaults and select the Access Control (IAM) tab > +Add > Add role assignment as seen below.
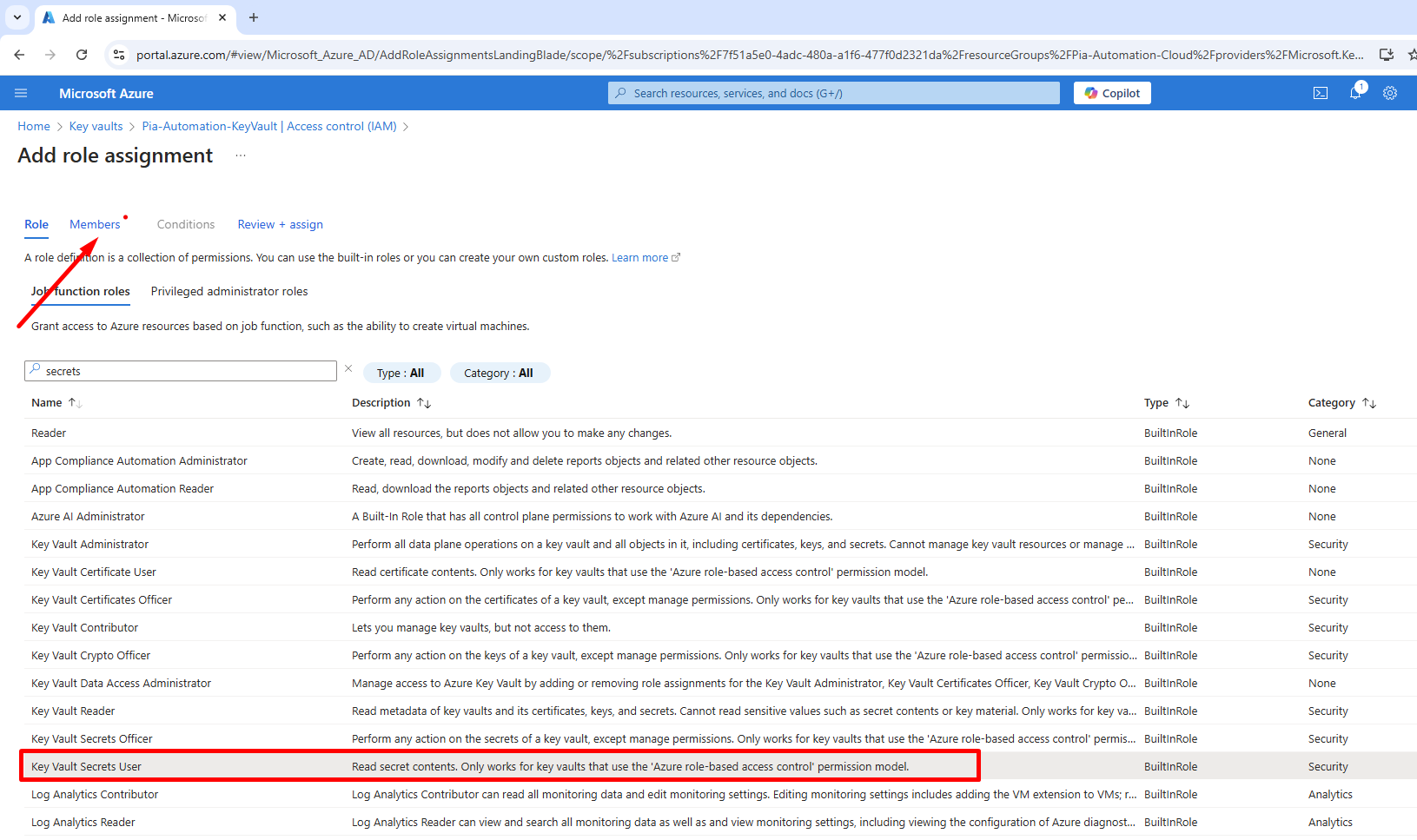
Within the Job function roles tab, search for "Key Vault Secrets User", select the role then select the "Members" tab.
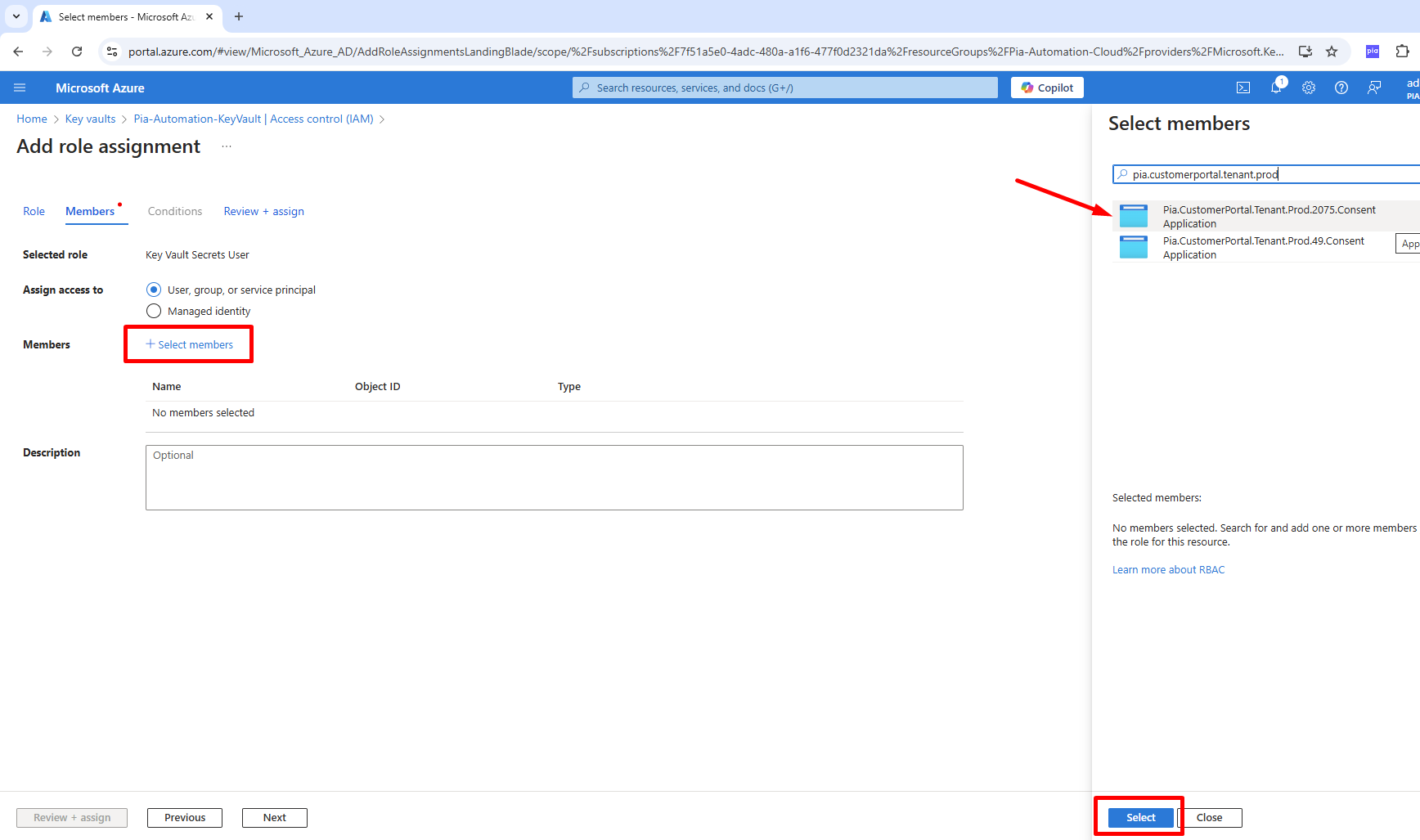
Click + Select members, then in the right hand pop-up search for your Pia application consent (which would be in the format of Pia.CustomerPortal.Tenant.Prod.<tenantId>.Consent), select it, then click the Select button, then click the Review + Assign button.
Step 3: Extension Automation Configuration
3a: Configure the Client Package Configuration
Head on over to your Pia Portal, navigate to Configuration > Clients and select the client you wish to configure Google Workspace integration form for, search for the Google Workspace: Create New User package.
Under the Configuration section, set the package Opt Mode to "Opt-In". Then select the cog icon within the Configuration panel to start configuring the automation.
Complete all the required (*) configuration values (feel free to leave the Azure Key Vault Secret Name as the default, this just indicates the name of the secret within the Azure Key Vault that you would have setup in Azure Key Vault Secret Creation).
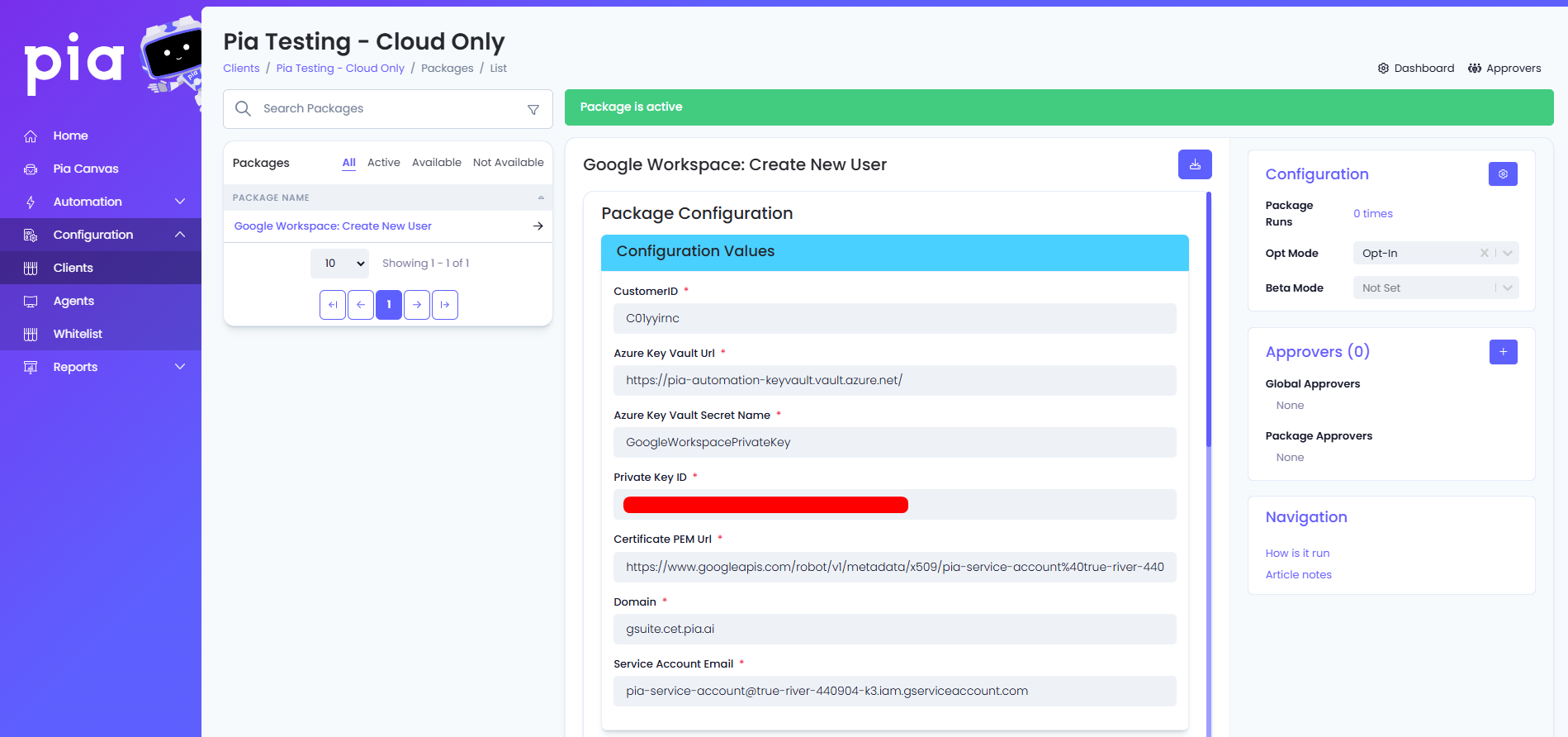
Most values will be found within the .json file created in the "Create a new key for your Service account" section of this Google Workspace Configuration tutorial (excluding the Customer ID, Google Workspace domain and the Azure Key Vault URL, for more instructions on where to find these values, please see below).
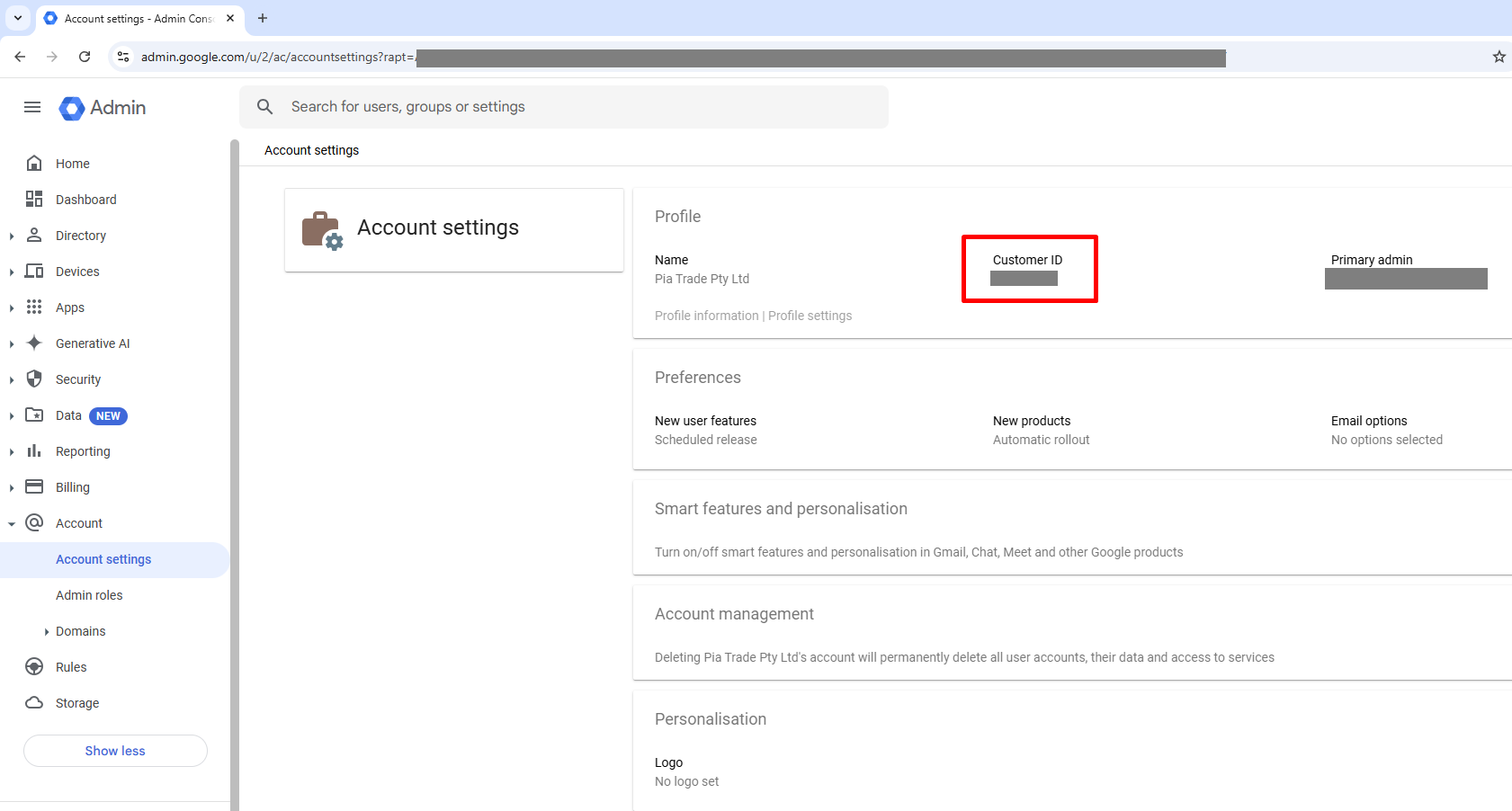
Copy the Customer ID from the Google Workspace Account Settings page.
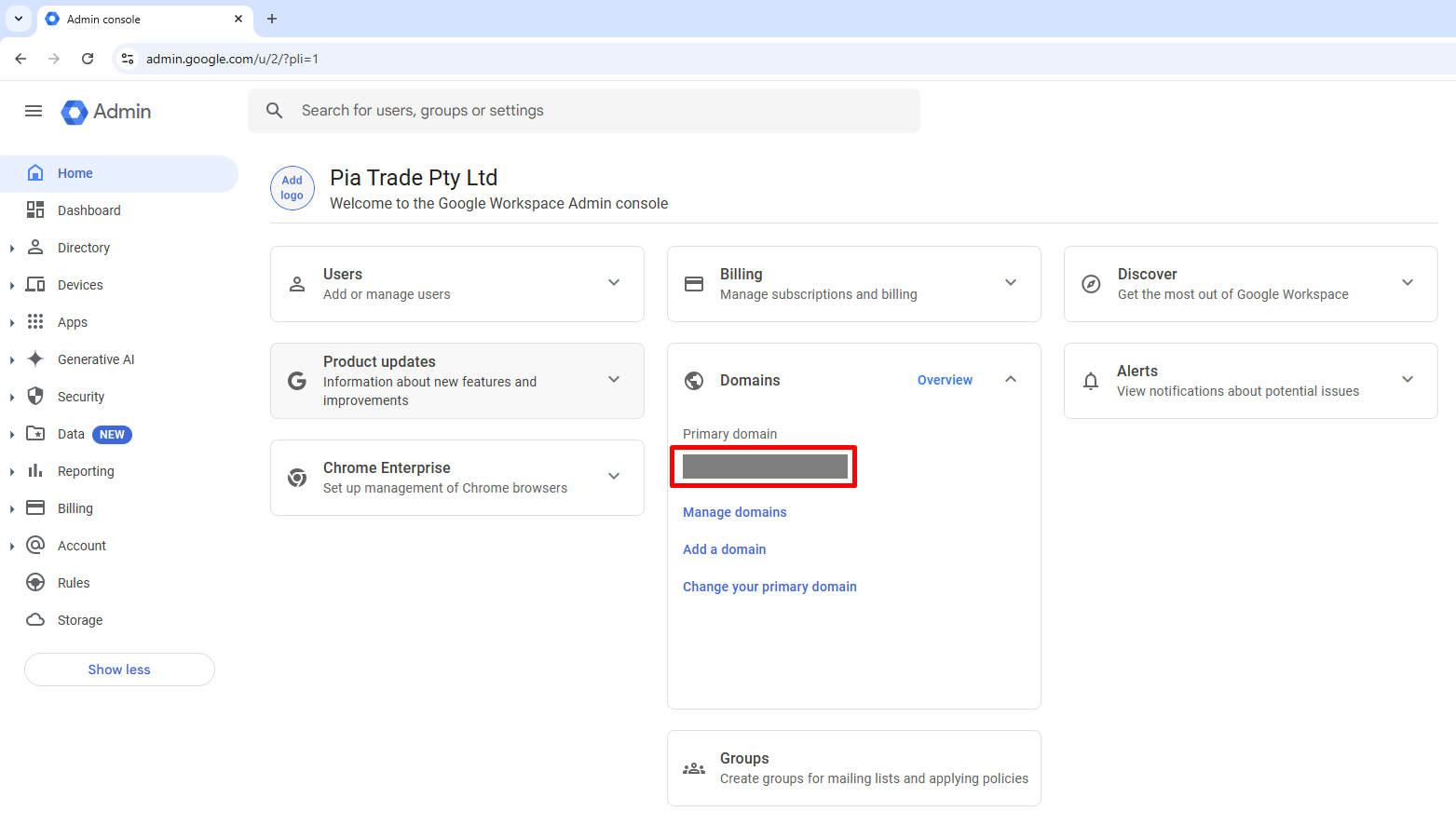
Copy the Primary domain from the Google Workspace Home Dashboard.
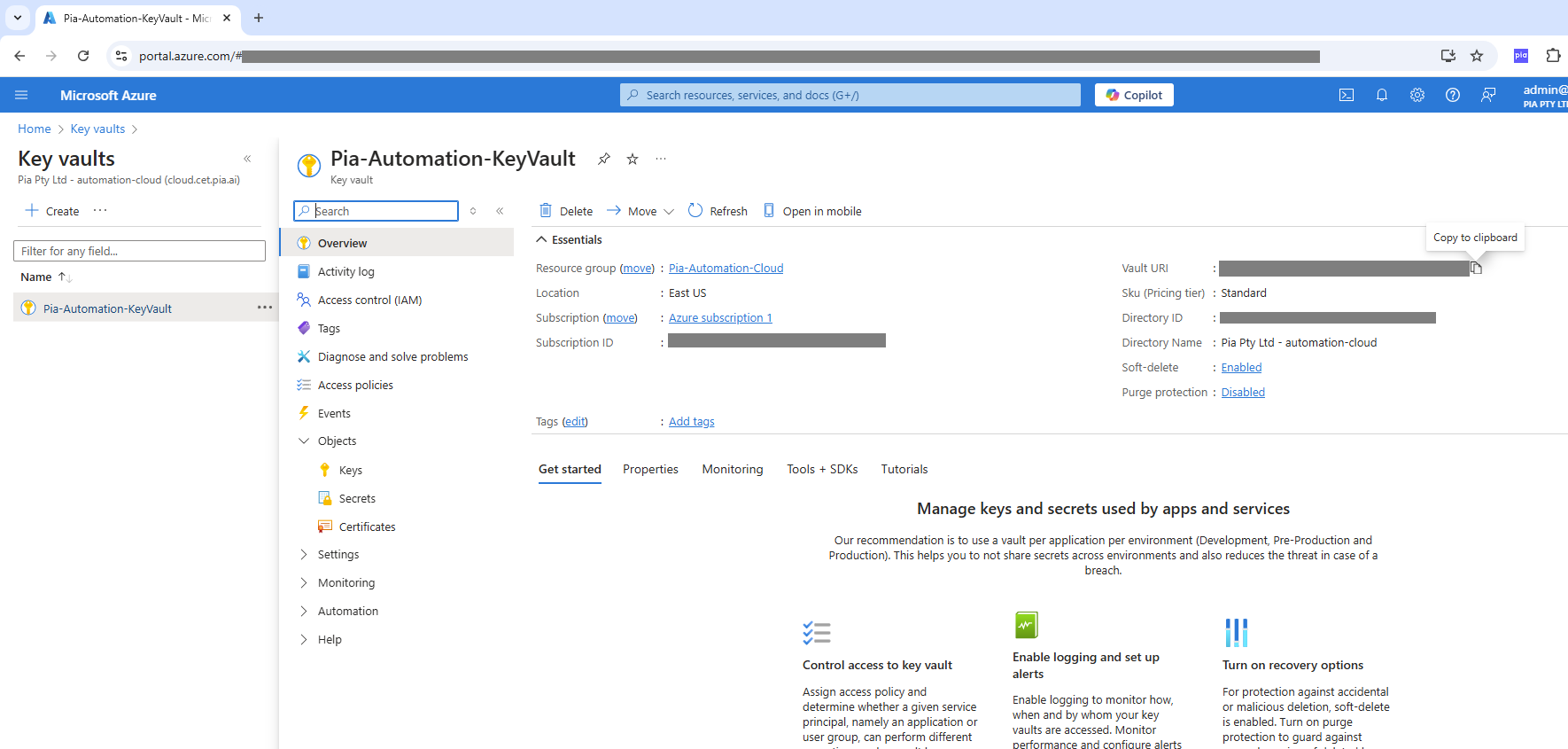
The Azure Key Vault URL will be found within the Azure Key Vault Dashboard as seen below.
3b: Appending the Extension Automation
Head over to the Staff Onboarding package configuration for your selected client, on the right hand side of the screen under Extension Points, select the small cog icon in the top right corner.
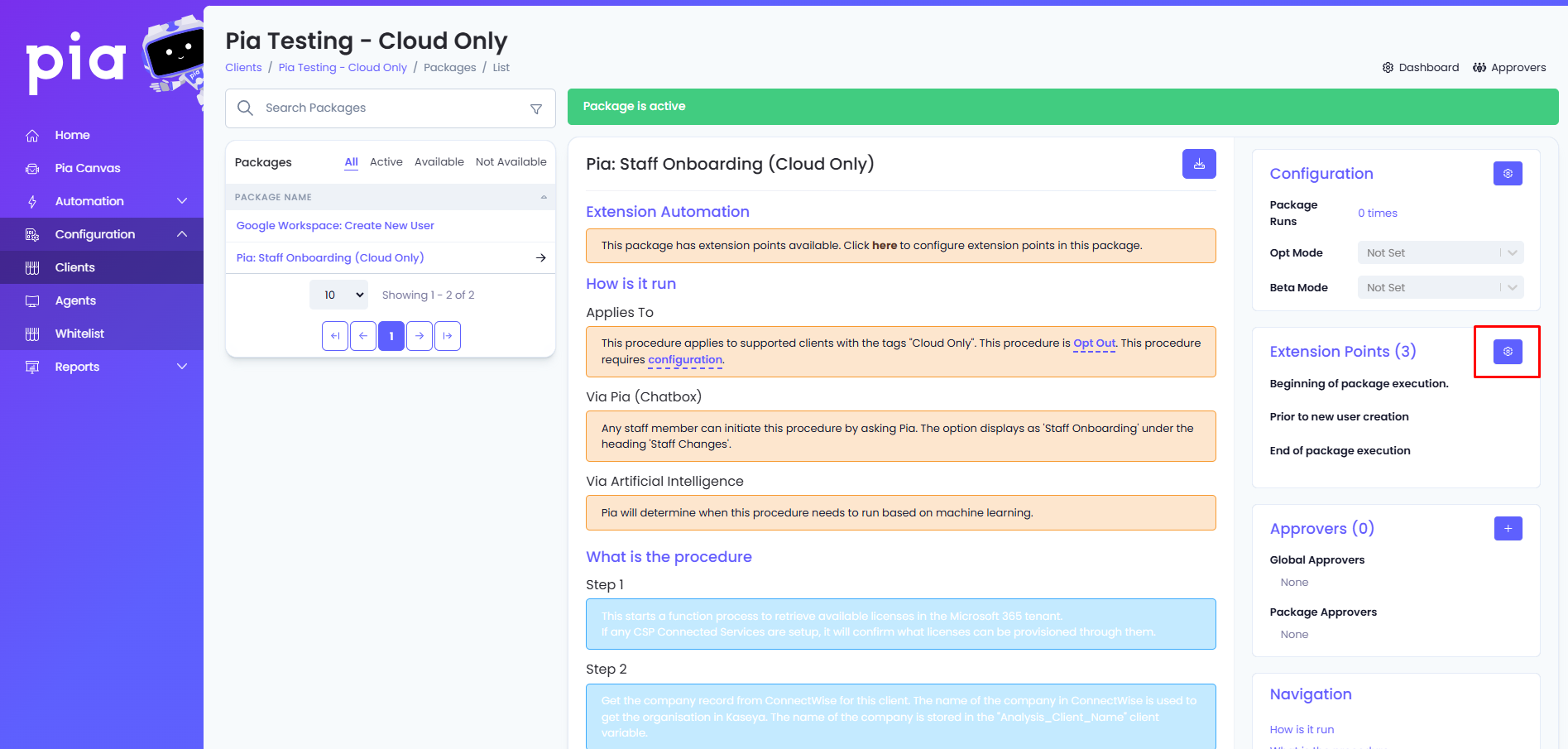
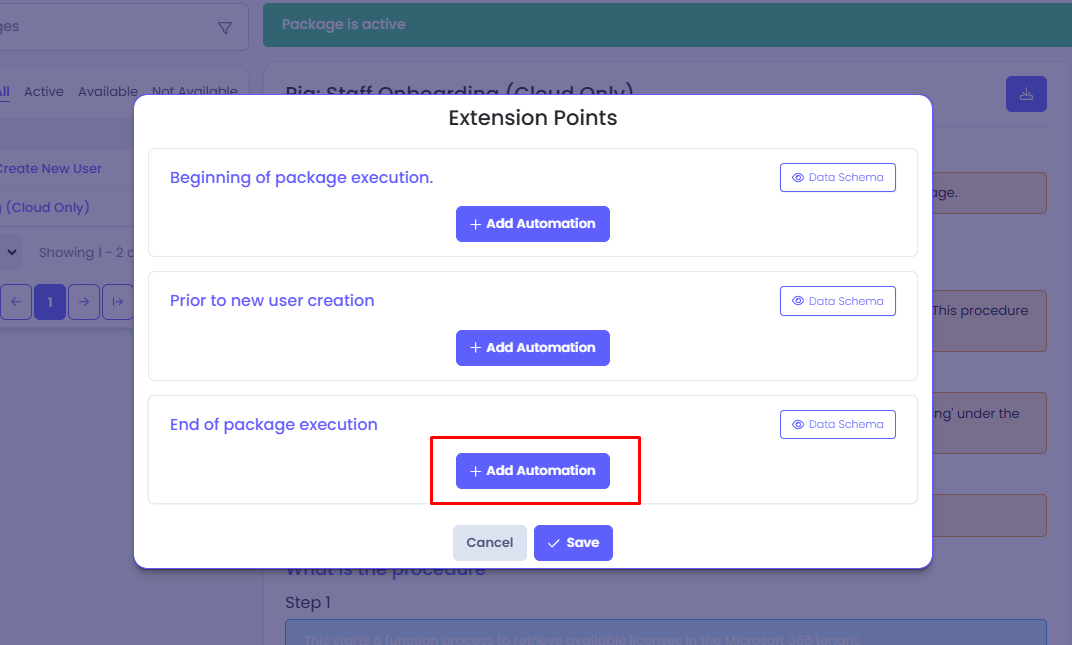
Select + Add Automation for the End of package execution point.
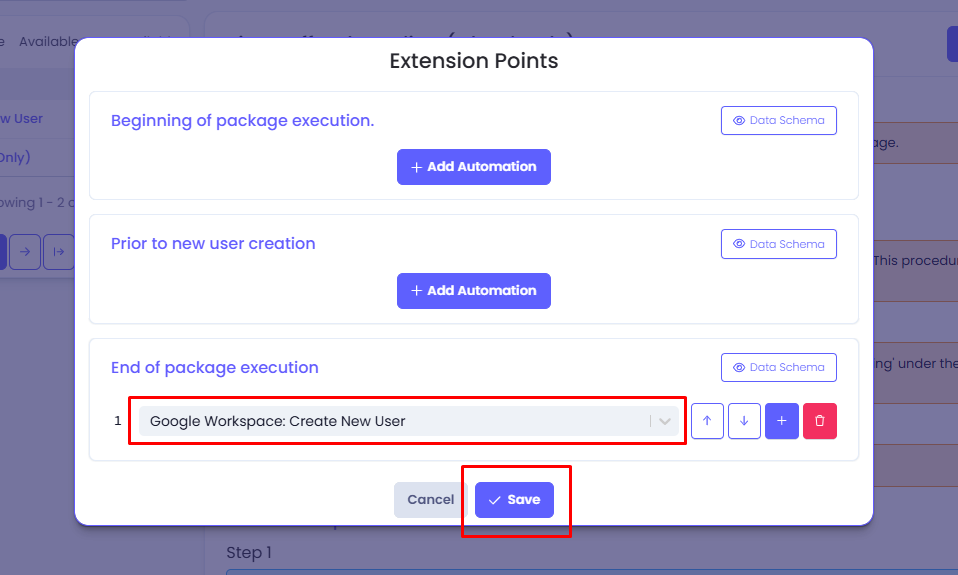
Select the Google Workspace: Create New User extension automation from the list of extension automations, then click Save.
And now you have completed the entire setup in order to use this extension automation!